...
The Parasoft Security Bundle is a package of tools for your DTP infrastructure that provide visibility into your security compliance efforts. The Security Bundle contains configurations that align the findings sent to DTP with security guidelines. It also includes specialized reporting mechanisms that enable you to demonstrate compliance with guidelines for auditing purposes.
The Security Bundle is available from the Parasoft market place in the customer portal. Refer to the Security Bundle documentation for installation instructions and other details.
...
Gating is the concept of preventing the code from being promoted to the next stage of the release pipeline. Some organizations implement gates during check-in. In a safety-critical industry, gating the check-in may be an acceptable workflow, but we recommend implementing gates during the CI process. Doing so removes barriers to developer productivity and enables feedback (i.e., static analysis violations associated with meaningful information) to loop back to developers more quickly. Additionally, the CI build typically provides more context to enrich the information.
Feedback as Guidance for Developers
...
Gating Source Control
You can configure your source control management (SCM) repository to trigger quality gates when developers check in their code. If you use git, for example, you can write a pre-commit git hook that runs Parasoft code analysis tools and aborts the commit if the violations are reported. Refer to the documentation for your source control tool for details on how to apply gates at the source control layer.
Parasoft integrates with popular source control systems and code repositories, which enables our tools to determine code authorship, scope of execution for incremental analysis, and to assign results to team members. Refer to the Appendix for supported systems.
Gating CI
You can configure your CI tool to apply quality gates as part of your build process. Parasoft integrates with several CI tools that enable you to visualize test execution and code analysis results from Parasoft tools in your continuous integration system interface. Refer to the Appendix for supported CI tools.
Configuring quality gates at the CI layer differs from system to system. The Parasoft Findings for Jenkins extension, for example, supports quality gate configuration from the UI. Refer to the documentation for your CI tool for details.
Feedback as Guidance for Developers
When viewed in the IDE or in DTP, code analysis violations include links to the documentation, which provides technical information and details about the potential impact of the programming patterns detected by the checkers. By providing detailed context about why violations are reported, developers gain a deeper understanding of the security issues associated with their code base. The guidance provided by the code analysis results, furthermore, is most effective when code analysis executes in the IDE before checking in the code.
Training for Secure Coding
Parasoft helps train your team on secure software development in a variety of ways. First, the rule checker documentation shipped with Parasoft DTP and code analysis tools provide thorough explanations of issues. It explains the security relevance, even if it’s not obvious, such as buffer overflows. They also include examples and links to resources, such as canonical sources from CERT, CWE, OWASP, etc.
Some documentation includes video and PDF training on specific violation topics. The resources are provided through our partnership with the Software Assurance Marketplace (SWaMP) and are free for our users.
Many checkers also include OWASP-specific training through our partnership with HackEDU. Contextual training for a specific static analysis violation is free and accessible from the documentation. Teams can also take advantage of the full security training and certification program available from HackEDU at an additional cost.
Finally, Parasoft offers training for our security solution available through several channels:
Customer portal: https://customer.training.parasoft.com. The training includes self-paced courses and knowledge-base articles.
- We post security-related information in our forums: https://forums.parasoft.com/
- We post security-related topics on our blog: https://www.parasoft.com/blog/?_sft_topic=security
- General documentation is available online at https://docs.parasoft.com
Define Compliance Policy
Compliance in your organization may mean that no static analysis violations are allowed when checking code against a specific set of guidelines, such as OWASP Top 10. Compliance may also mean zero violations for only specific parts of the code . . . or for specific guidelines within a standard that you've determined to be critical to your project.
...
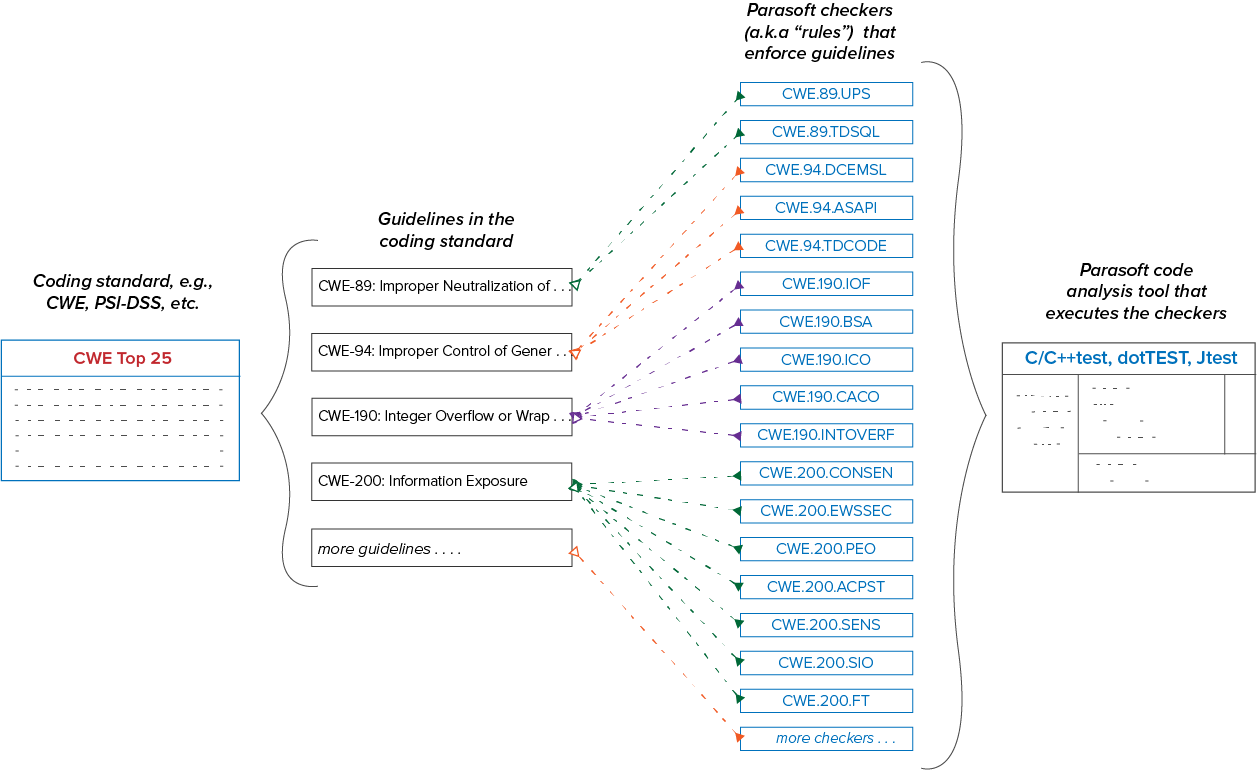
Parasoft supports compliance initiatives with advanced code analysis and reporting technologies. Parasoft tools check the code for specific patterns that are known to result in software defects. The checkers (also called static analysis rules) map to guidelines within a standard. More than one checker may be required to verify that the code meets a guideline. Conversely, more than one guideline may rely on a single checker. Refer to the Glossary of Terms for more detailed definitions of standards and guidelines.
The mapping between Parasoft checkers and coding guidelines may have an impact on how you define compliance in your organization. A checker may report violations for guidelines that are critical to your application, as well as guidelines that are less relevant. This is why the ability to suppress violations (deviate from the standard) is important. Deviations are discussed in greater detail in the Documenting Deviations section.
...
You can also automate ticket creation either by using the REST API or by creating a custom workflow with Extension Designer. If you choose to fully automate ticket creation, make sure that you've fully tested your scripts, including error conditions, to avoid accidentally create thousands of tickets. If you choose to leverage this functionality, creating tickets manually is the recommended workflowof tickets. If you choose to leverage this functionality, creating tickets manually is the recommended workflow.
Configuring for Traceability
Deploy the Parasoft Traceability Pack for deeper integration with ALM systems. The integration includes traceability reporting for demonstrating traceability from test automation (including DAST results) and code analysis (including SAST results) to work items documented in the ALM. This enables you to associate security testing outcomes with the application's business requirements. This kind of full requirement traceability is necessary for audit and compliance in many safety-critical industries.
Documenting Deviations
When you need to deviate from the security standard, you can apply a suppression in DTP or in the code from the desktop instance of your analysis tool. Suppressing a violation means that the defect pattern is acceptable in this specific instance and that you are going to ignore the violations reported by the tool for the foreseeable future.
...
DTP allows you to subset findings associated with a project by creating filters. For each project defined in DTP, a default filter with the same name of the project is created. Filters can have different run configurations, teams, and resource groups.have different run configurations, teams, and resource groups.
A resource group is a collection of resources (i.e., files and/or folders) defined by a set of one or more Ant file patterns. Resource groups enable more granular views of the data associated with a filter. After associating a resource group with a filter, the data presented in all widgets, reports, and explorer views for static analysis violations and metrics results will be narrowed according to the defined pattern.
Refer to the DTP documentation for details.
Integrating SCA to Secure Open Source
Software Composition Analysis (SCA) is an important part of incorporating open source (OSS) into your application. SCA checks your software for OSS components and compares them against known security vulnerabilities, such as CVE and NVD. SCA tools report which versions of software you’re running that should be updated or patched. This helps prevent your application from shipping with known vulnerabilities. OWASP Top 10 requires the use of SCA per the A9 “Using components with known vulnerabilities” guideline.
OWASP also makes an SCA tool, called the OWASP dependency check, that identifies vulnerabilities for Java and .NET code. You can deploy the OWASP Dependency Check Pack to DTP, which will enable DTP to accept data from OWASP dependency check and integrate the information into an OWASP Top 10-specific dashboard. The information will be also be included in the OWASP compliance report.
A resource group is a collection of resources (i.e., files and/or folders) defined by a set of one or more Ant file patterns. Resource groups enable more granular views of the data associated with a filter. After associating a resource group with a filter, the data presented in all widgets, reports, and explorer views for static analysis violations and metrics results will be narrowed according to the defined pattern.
Refer to the DTP documentation for details.
Advanced Configuration and Strategies
...
The following sections describe the supported components for enabling Parasoft's Security Compliance solution.
Supported Languages
Out of the box, Parasoft supports Parasoft can analyze the following languages out of the box:
- Java
- .NET-based languages
- C
- C++
- C#
- VB.NET
- HTML
- CSS
- XML
Parasoft supports several other programming languages via the Parasoft Multi-Language Pack:
- Android-based applications
- Apex
- Go
- Groovy
- JavaScript
- Kotlin
- Objective-C
- PHP
- Python
- Ruby
- Scala
- Swift
- Typescript
Contact your The Parasoft representative for Parasoft Multi-Language Pack download and license informationPack is available in the marketplace on the Parasoft customer portal.
DTP and Enterprise Pack 2020.1
Standards |
|
|---|---|
Parasoft tools |
|
Continuous integration | Parasoft can report static analysis violations in the following CI systems:
You can integrate with other CI systems using the command line interface. |
Source control | Refer to the tool documentation for supported SCMs: |
DTP and Enterprise Pack 5.4.3
...