In this section:
Introduction
Reverse proxies are sometimes used to ensure high availability or strengthen network security. You can run DTP in a reverse proxy environment by configuring the reverse proxy server to forward user requests to the port where the applications are hosted. Additionally, you must either configure the reverse proxy server to send the required headers to DTP or update the DTP Tomcat server configuration.
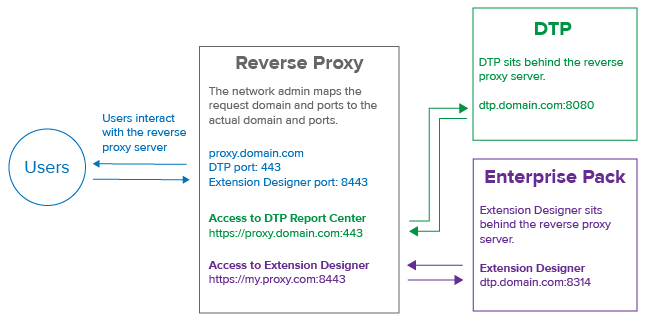
The following diagram shows the basic reverse proxy flow.
Configuration Option 1 - Sending Headers
Configure your reverse proxy to send the following headers to DTP:
- X-Forwarded-Host
- X-Forwarded-Proto
- X-Forwarded-For
- Host
The X-Forwarded-For header is used by DTP Enterprise Pack. See Network Settings for additional information about using DTP Enterprise Pack in a reverse proxy environment.
The Host header should be the host of the original request, i.e., the reverse proxy host.
Configuration Option 2 - Tomcat Server Configuration
You can configure the Tomcat server configuration file to enable DTP to function in a reverse proxy environment.
Add another
Connectorelement to the INSTALL_ROOT/tomcat/conf/server.xml file. This element must be the last Connector element in the server.xml file.<Connector URIEncoding="UTF-8" acceptCount="10" compressableMimeType="text/ html,text/xml,text/plain" compression="on" compressionMinSize="128" connectionTimeout="60000" debug="99" disableUploadTimeout="true" enableLookups="true" maxSpareThreads="75" maxThreads="150" minSpareThreads="25" port="8888" proxyName="proxy.parasoft.com" proxyPort="8443" scheme="https" secure="true"/>
- Modify the following attributes:
- port: the port on DTP server to which the proxy server sends the request
- proxyName: hostname of the proxy server
- proxyPort: port on proxy server
- scheme: scheme on proxy server (https or http)
- secure: set to true if the scheme is https and false if scheme is http
In the example Connector element in step 1, DTP will receive HTTP requests on port 8888 from a proxy server configured at https://proxy.parasoft.com:8443.
Forwarding Requests
Refer to your reverse proxy server documentation for details on how to forward requests. The following examples show how a reverse proxy may be configured on nginx.
Forwarding Configuration for DTP
# DTP: HTTPS 3001 -> HTTPS 8443
server {
listen 3001 ssl;
listen [::]:3001 ssl;
ssl on;
ssl_certificate /etc/nginx/certs/ssl-certificate-bundle.crt;
ssl_certificate_key /etc/nginx/certs/ssl-certificate-key.key;
ssl_session_cache builtin:1000 shared:SSL:10m;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_ciphers HIGH:!aNULL:!eNULL:!EXPORT:!CAMELLIA:!DES:!MD5:!PSK:!RC4;
ssl_prefer_server_ciphers on;
location / {
proxy_pass https://dtp.yourcompany.com:8443;
proxy_set_header Host $http_host;
proxy_set_header X-Forwarded-Host $http_host;
proxy_set_header X-Forwarded-Proto https;
proxy_read_timeout 90;
}
}
Forwarding Configuration for Enterprise Pack
See Network Settings for additional information about using DTP Enterprise Pack in a reverse proxy environment.
# Enterprise Pack: HTTPS 3002 -> HTTP 8314
server {
listen 3002 ssl;
listen [::]:3002 ssl;
ssl on;
ssl_certificate /etc/nginx/certs/ssl-certificate-bundle.crt;
ssl_certificate_key /etc/nginx/certs/ssl-certificate-key.key;
ssl_session_cache builtin:1000 shared:SSL:10m;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_ciphers HIGH:!aNULL:!eNULL:!EXPORT:!CAMELLIA:!DES:!MD5:!PSK:!RC4;
ssl_prefer_server_ciphers on;
location / {
proxy_pass http://entpack.yourcompany.com:8314;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Host $http_host;
proxy_set_header X-Forwarded-Proto https;
proxy_read_timeout 90;
# websocket
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection "upgrade";
}
}
Forwarding Configuration for Data Collector
See Configuring Data Collector for additional information about using Data Collector in a reverse proxy environment.
# Data Collector: HTTPS 3003 -> HTTPS 8082
server {
listen 3003 ssl;
listen [::]:3003 ssl;
ssl on;
ssl_certificate /etc/nginx/certs/ssl-certificate-bundle.crt;
ssl_certificate_key /etc/nginx/certs/ssl-certificate-key.key;
ssl_session_cache builtin:1000 shared:SSL:10m;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_ciphers HIGH:!aNULL:!eNULL:!EXPORT:!CAMELLIA:!DES:!MD5:!PSK:!RC4;
ssl_prefer_server_ciphers on;
location / {
proxy_pass https://dc.yourcompany.com:8082;
proxy_set_header X-Forwarded-Host $http_host;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_read_timeout 90;
}
}
Reverse Proxy Support for WebSockets
See the following documentation to configure your reverse proxy server for WebSockets communication: http://nginx.org/en/docs/http/websocket.html
Known Issues and Constraints
- Reverse proxy path mappings must be exact in order for the UI to work. For example, the proxy address "https://proxy.parasoft.com/grs" must correlate to the DTP server address "https://server.parasoft.com/grs". Mapping "https://proxy.parasoft.com/proxy/grs" to "https://server.parasoft.com/grs" will fail.
- When calling /v1/dtpServices through the proxy server, Data Collector URLs will default to port 8082 on the proxy server, which may not be open. We assume that Parasoft code analysis and test execution tools accessing Data Collector will access its URL directly and not through the proxy server.
- JMS Event Broker URLs will not be accessible through the proxy server because the proxy server’s ports are not JMS ports 43 Reverse Proxy Support.
- The login redirect is based on the actual DTP server and not the proxy server. For example, if the proxy server receives via HTTPS and forwards via HTTP, then the browser will be redirected via HTTP instead of HTTPS.